
Sacks of rocks: Lighten your PCI DSS reporting load
OK, an apology to start with: This post is about

No organisation has infinite budget or staff and what’s risky for one business (say, a law firm) is different to what is risky for another (say, a hospital). Risk-based controls are tailored to your specific environment. Your threats, your vulnerabilities, and your business impact: your risk!
Don’t just take our word for it: Insurers and standards like ISO 27001 and the PCI DSS all demand that businesses assess and treat risks, which implies the application of effective, risk-based, controls.
No silver bullets. No solutions looking for a problem. Just the effective reduction of business risk through the application of requirements-driven controls.

DotSec has, for over 25 years, worked closely with a wide range of corporate and government organisations, providing cyber security services in areas ranging from ISO 27001, IRAP and PCI DSS compliance and certification,to penetration testing, maturity assessments, incident detection and response, and best-practice guidelines.
Our Managed Detection and Response (MDR) and Managed Security Information and Even Management (MSIEM) service combines near-real time endpoint threat detection with long-term even analysis and trend reporting, helping our clients to remain secure and meet their various insurance and compliance requirements.
SIEM (with its ability to provide detailed historical, risk and priority-based correlation, analysis and reporting) continues to be a core component in any mature cyber security architecture.
We also understand that analysis of historical events addresses only half the problem, and that organisations need better capabilities for proactive endpoint protection. Accordingly, we have extended our MSIEM service to include Managed Endpoint Detection and Response (MEDR) to provide near-real time endpoint threat detection. Log events are collected by the endpoint sensor and are analysed in near-real time, resulting in high-fidelity alerts and endpoint protection.
Based on our own adversary emulation testing and our commercial experience to date, we are confident that our MDR+MSIEM service, based on the market-leading capabilities of CrowdStrike and Splunk, provides our clients with the most capable and effective incident management service available, and we look forward to assisting you with our expanded capabilities.

We help organisations to manage the risks associated with encryption, cryptographic key management and related services by supporting the deployment of secure hardware-backed environments for key storage and cryptographic processing.
The implementation of risk-based cryptographic controls will also help to ensure compliance with regulatory standards including ISO/IEC 27001 (defined cryptographic controls and formal processes for the secure lifecycle management of encryption keys) and the Payment Card Industry Data Security Standard (protection of stored account data through strong encryption) and the Australian Government’s Information Security Manual (ISM).
By implementing secure key management services (KMS), we enable organisations to centralise and control the lifecycle of cryptographic keys, from generation to use, rotation, and revocation, with robust access control and audit mechanisms. This supports risk-based controls by ensuring that only authorised entities have access to sensitive cryptographic material.
We also assist with securing data at rest by supporting filesystem-level encryption, enabling sensitive data to be encrypted automatically without requiring application-level changes supporting both transparent database encryption (TDE) and client-side encryption (CSE) strategies, supporting both on-prem and cloud/hosted environments.
Together, these capabilities enable organisations to implement strong, risk-aligned cryptographic controls, significantly reducing exposure to risks associated with third-party data handling, while also enhancing compliance with data sovereignty, data-loss prevention (DLP) and client-confidentiality requirements.









Where needed, we assist in creating a secure Standard Operating Environment (SOE) based on CIS Build Kits or Microsoft Intune, ensuring that baseline configurations are repeatable, supportable, and aligned with risk management and compliance objectives.
We help organisations to harden their Microsoft 365, Azure, and Windows environments by delivering secure configuration-improvement services using techniques and recommendations that are aligned with recognised vendor guidelines and international security frameworks.
For Microsoft 365 environments, we provide hardening services that focus on Exchange Online, SharePoint, Teams, and Purview. The hardening guidelines focus on identity management, data protection, and threat mitigation sections and references from the ISO/IEC 27001 (A.5.18, A.8.16) and the Australian Information Security Manual (ISM) cryptographic and access control guidelines. Remediation steps follow the CIS benchmark recommendations, ensuring changes are risk-informed and verifiable.
For Microsoft Azure, we provide hardening recommendations for cloud workloads against the CIS Azure Foundations Benchmark, supplemented by service-specific benchmarks.
Pre-hardening assessment encompasses governance, networking, storage, and identity configurations, providing a risk-based view of security gaps and aligning findings with obligations under relevant standards and guidelines.
For Microsoft Windows servers and workstations, we provide hardening guidelines for Windows 11, Server 2022, and 2025.
Many organisations, from banks and superannuation funds to law firms and schools, develop software in-house. This software is essential for business-specific functions but even well-tested code may contain vulnerabilities that only emerge in production, between development cycles and/or between penetration tests.
DotSec provides a fully managed Web Application Firewall (WAF) service that provides a critical first line of defence, helping to protect your online services against application-layer attacks.
Our managed WAF service also helps meet key requirements under frameworks such as PCI DSS (Control 6.4) and controls from the Australian Government Information Security Manual (ISM).
Everyone makes mistakes and even mature development teams can slip up and accidentally introduce the kinds of vulnerabilities that feature in the OWASP Top 10. A managed WAF mitigates these threats in real time, reducing the attack surface while longer-term improvements are made through code reviews, security testing, and penetration testing.
Importantly, the WAF integrates seamlessly with our MDR and MSIEM services, delivering not only real-time threat detection but also proactive risk mitigation across the web application layer. This integrated approach enhances security visibility and strengthens an organisation’s ability to meet regulatory, insurance, and operational requirements.
With DotSec’s 25 years of operational experience, we’re able we deliver a robust, compliant, and effective WAF solution that will help to defend your web applications and support your broader cybersecurity risk-management strategy.
Security frameworks and standards exist to provide a common point of reference, allowing an organisation to be confident of its own security maturity while also being able to demonstrate that maturity to a client, partner, insurer or other third party. In a study conducted by DotSec and Momentum Media, 70 per cent of survey’d law firms were either unsure if that they complied with no well-accepted standard or framework such as such as ISO/IEC 27001:2022 or the CIS Critical Controls.
An organisation that fails to comply with a well-accepted, national or international standard or framework will almost certainly fail to have a holistic set of cyber security policies, procedures and controls in place. This, in turn, makes the attacker’s job unnecessarily easy, and may also open the organisation up to accusations of failure to meet best practices, especially in the event of a security breach

OK, an apology to start with: This post is about
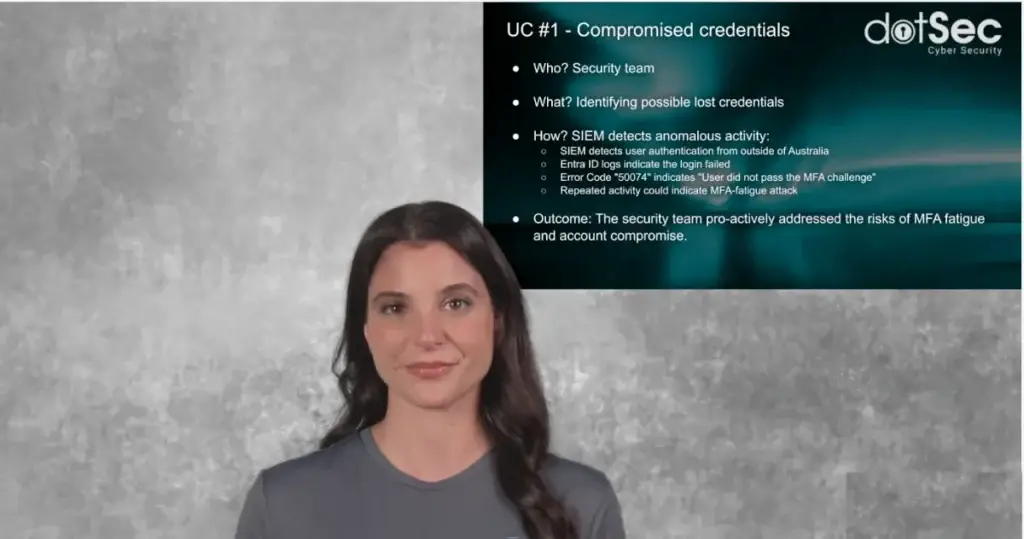
One video: Four SIEM use-cases in eight minutes! Security Information