
Sacks of rocks: Lighten your PCI DSS reporting load
OK, an apology to start with: This post is about

In cybersecurity, knowing where you stand is half the battle. DotSec will work with you to uncover and prioritise your organisation’s risks based on operational realities, compliance requirements, and business goals.
We conduct structured assessments aligned with recognised standards — ISO 27001, PCI DSS, the CIS Critical Controls, or the ACSC Essential Eight — helping you identify systemic weaknesses, scope compliance efforts, and make confident, risk-informed decisions.
No silver bullets. No guesswork. Just clear identification and prioritisation of risk.
ISO/IEC 27001 is the internationally recognised standard for establishing, implementing, and maintaining an effective information security management system (ISMS). It defines the frameworks, processes, and organisational structures required to manage information security risks, and is adaptable to organisations of all sizes and industries.
Achieving ISO 27001 accreditation demonstrates a commitment to robust information security practices and risk management. It goes beyond simply deploying security products, emphasising continual improvement and systematic risk analysis to meet evolving threats and regulatory expectations.
dotSec’s team includes ISO 27001 lead implementers and lead assessors, and dotSec itself is ISO 27001-certified. We have deep expertise in interpreting ISO 27001 requirements and translating them into practical, defensible security programs that stand up to audit and real-world scrutiny.
We work closely with clients to build and maintain functioning ISMS frameworks that support ISO 27001 compliance and prepare organisations for successful ISO 27001 certification. Our services give you a competitive advantage when negotiating contracts, reassuring clients and business partners who prioritise cybersecurity and risk governance.
With DotSec’s support, you’ll streamline your path to ISO 27001 accreditation — allowing your business to demonstrate security leadership, simplify client onboarding, and eliminate the need to build confidence in your security practices from scratch with every new engagement.
The Payment Card Industry Data Security Standard (PCI DSS) is the recognised benchmark for protecting cardholder data and reducing credit card fraud. It applies to all organisations that store, process, or transmit payment card information, including merchants, in-scope service providers, and financial institutions, and forms the foundation of payment card industry PCI compliance.
DotSec is a PCI DSS-compliant service provider, with firsthand experience achieving and maintaining compliance with this demanding standard. We understand the unique challenges businesses face in meeting the Payment Card Industry Data Security Standard requirements, particularly under Australian regulatory expectations.
If your business processes payment card data, or if you are a service provider that can affect the security of the merchant’s in-scope systems, then you are bound by a merchant agreement, typically with a financial institution like the Commonwealth Bank of Australia (CBA), which requires you to maintain PCI DSS compliance and demonstrate it when requested.
Failure to comply increases the risk of higher merchant fees, greater reporting costs, breach recovery expenses, and, in extreme cases, suspension of merchant privileges.
dotSec’s information security services are designed to help you reduce the risks associated with PCI DSS non-compliance. We work with you to meet your reporting obligations and maintain strong, defensible security controls — ensuring your business stays aligned with the Payment Card Industry Data Security Standard requirements.
DotSec’s Capability Maturity Assessment provides a structured evaluation of your organisation’s information security maturity, benchmarked against recognised industry frameworks. A Capability Maturity Assessment measures how well your security processes and controls are designed, managed, and improved over time, helping you benchmark against standards and build a roadmap for improvement.
Our assessments are generally (depending on customer requirements; the NIST CSF is another option) conducted with reference to selected controls from the CIS Critical Security Controls (v8.1), ISO/IEC 27002:2022, and the Australian Privacy Principles (APPs).
The CIS Critical Security Controls framework defines 18 essential cybersecurity Controls, each broken down into multiple Safeguards. These Safeguards are grouped into three Implementation Groups (IGs) to help organisations prioritise security improvements based on their size, resources, and risk profile. The CIS Critical Controls offer a practical, technically focused baseline that addresses a broad range of security domains.
However, while the CIS Controls deliver excellent technical coverage, they do not fully address Governance, Risk, and Compliance (GRC) or privacy management.
To ensure a complete picture, DotSec’s assessment also incorporates key GRC and privacy controls drawn from ISO/IEC 27002:2022 and the Australian Privacy Principles.
With DotSec’s guidance, your organisation will gain a clear view of its current maturity, identify critical gaps, and prioritise improvements, building a defensible, standards-based cybersecurity improvement plan.
A Cyber Security Tabletop Exercises (TTXs) is a highly interactive and engaging activity, that is designed to test your organisation’s incident response plan, capabilities and processes. A TTX provides a safe and controlled environment for the organisation to practise it’s incident detection, containment and response strategies, and identify areas of weakness that need to be addressed.
Cyber Security Tabletop Exercises (TTXs) are essentially simulations of potential incidents (in this case, cyber incidents) that could impact an organisation, and the generally form part of the organisation’s incident response plan and process because they allow organisations to proactively prepare for incidents rather than reactively responding to them.
By conducting TTXs, your organisation can test it’s incident response strategies and practices, without the interruption and cost associated with an adversary emulation test.
Note that a TTX is not intented as a substitute for a pen test or an adversary emulation exercises; a TTX is a risk management exercise that is designed to identify risks associated with incident-management policies and procedures while a pen test or adversary emulation exercise is intended to test the effectiveness of the controls that have been put in place following a TTX-based risk identification and treatment program.
If the TTX identifies any gaps or areas of improvement, those gaps can then be addressed before a pen test or adversary emulation exercise takes place. This proactive approach can significantly enhance an organisation’s incident response capabilities and increase its resilience when actual cyber incidents take place.
Security frameworks and standards exist to provide a common point of reference, allowing an organisation to be confident of its own security maturity while also being able to demonstrate that maturity to a client, partner, insurer or other third party. In a study conducted by DotSec and Momentum Media, 70 per cent of survey’d law firms were either unsure if that they complied with no well-accepted standard or framework such as such as ISO/IEC 27001:2022 or the CIS Critical Controls.
An organisation that fails to comply with a well-accepted, national or international standard or framework will almost certainly fail to have a holistic set of cyber security policies, procedures and controls in place. This, in turn, makes the attacker’s job unnecessarily easy, and may also open the organisation up to accusations of failure to meet best practices, especially in the event of a security breach

OK, an apology to start with: This post is about
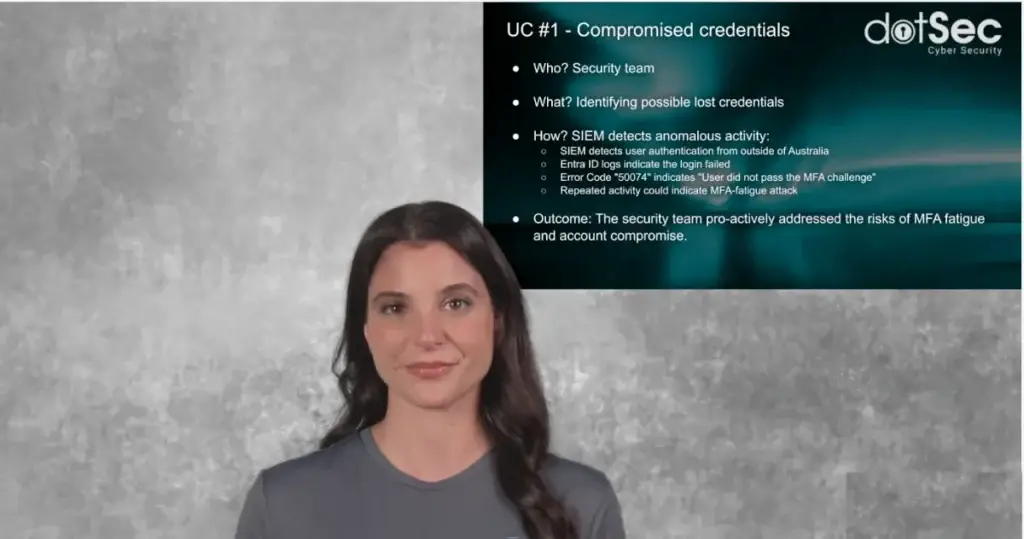
One video: Four SIEM use-cases in eight minutes! Security Information